In September 2017 a Norwegian vessel reported GPS jamming east of Finmark, close to an active Russian helicopter wing. Jamming was confirmed later by data analysis of helicopter acquired data.
In 2013 a team led by Todd Humphreys, Professor at the University of Texas in Austin, USA, spoofed GPS on a $80M yacht, moving it several hundred metres- -without ship systems detecting the change, whilst in February 2017 hackers allegedly took control of negation systems on a German owned 8,250 ton container vessel for 10 hours on route from Cyprus to Djibouti.
By Christopher Lavers*
Jamming of GNSS/GPS directly impacts various navigation-related systems including: ECDIS, AIS, Autopilot and VTS. However, subtle tampering of AIS and other systems may be more effective, as maritime users may not even know they are being manipulated.
According to Tor Svensen, previous maritime CEO at DNV GL, the industry has seen its first cyber events including manipulation of AIS, ECDIS and GPS data. In 2017 more than 50 cyber security incidents were detected in the Norwegian energy and oil and gas sector alone. Regarded as a Tier 1 National UK threat, a maritime cyber-attack could cost companies and the UK millions of pounds in financial terms alone.
But what is AIS? The Automatic Identification System, or AIS, is an automatic tracking system used on ships and Vessel Traffic Services (VTS) to identify and locate vessels by electronically exchanging data with nearby ships. It is used extensively in the maritime world, and mandated aboard all ships of 300+ gross tonnage. AIS transponders (on vessel stations) include a GPS receiver to collect vessel position and movement details.
Position and movement (e.g. course and speed) along with other information provided by the crew are automatically broadcast at regular intervals via a built-in transmitter using 2 VHF channels (161.975 and 162.025 MHz). AIS data can be processed and depicted on chart plotters or computers. One limitation of AIS is earth curvature, limiting horizontal range to c. 70km from shore, so information is only available around coastal zones or on a ship-to-ship basis. Since the mid-2000s companies have detected AIS transmissions with satellite-based receivers (S-AIS).
Using satellites solves the range problem, whereby a ship’s identity is recorded and decoded by satellite and sent to ground stations for processing and distribution. This method significantly increases the number of potential vessels within a satellite’s footprint. Companies such as exactEarth and Spire, and government programs have deployed AIS receivers on satellites.
AIS applications include: collision avoidance; fishing fleet monitoring and control; VTS; maritime security; Aids to Navigation; search and rescue; accident investigation; ocean currents estimates; infrastructure protection; besides fleet and cargo tracking.
AIS is used by many organisations and individuals, including: Port Authorities, Ship Owners, Managers and Builders, Brokers and Charterers, Tug Operators and Pilots, Search and Rescue Teams, Vessels’ Crews and Families’ Members, Coast Guard and Border Patrol, Recreational Sailors, Environmental Protection Agents, Maritime Enthusiasts, Radio-amateurs, and others.
Our ongoing Plymouth University assessment of the maritime sensors market has consulted many key maritime actors. The importance of AIS in the mind of the Qatari maritime professional for example, is seen in figure 1. This question has particular relevance when considering how AIS data provision impact similar data frequency expectation of satellite-based sensors’ data.
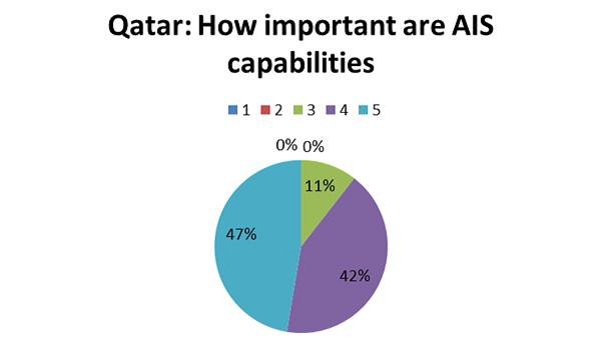
Figure 1: How important are AIS Capabilities. Users were asked: “On a scale from 1 to 5 how important are AIS capabilities to your organisation’s operations, where 1 is Not at all important, to 5 Very Important?”
We received some Middle Eastern AIS responses concerning persistency where Persistency is defined as “the ability to provide continuous maritime and littoral surveillance of any chosen area”. Comments included: “A valid problem of persisting without AIS algorithms … would provide too much data for use to meaningfully interpret.” Another common criticism was “We do not have the capacity to process data faster than weekly, except in crisis conditions following a piracy incident.” Such comments raise issues such as altering or stopping AIS algorithm function so meaningful interpretation is impossible, or overwhelming the system with higher than normal data levels.
We gauged the perception of the importance of space-based sensing and communications capabilities from various maritime professional groups. The response from 33 UK maritime professionals provided overwhelming evidence of the importance associated with GPS, as the single-most important space-based capability (figure 2). Whether end-users are right to give this emphasis on this space-based capability above all others is another question.
Governmental AIS users have also expressed their expectations that they can reasonably ask for near-real time space-based SAR (i.e. seconds)! SAR providers, produce more modest update time-frames. Overall the responses are representative of the space-based sensors market
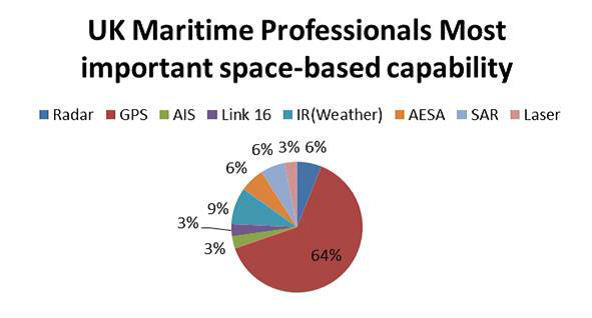
Figure 2: Most important space-based capability
The financial lure to compromise the AIS market is great. AIS, and other navigation-related systems, are big growth areas today. Using sources and information from various stakeholders we estimated the world AIS market expenditure (including S-AIS) over the 2014/15 period.
The AIS market was calculated between $174.5-226.9m, based on analysis using the total number of registered vessels (over 1,000 DWT) (deadweight tonnage) against total world DWT, which according to Statista (2015) gave 50,420 vessels globally. The average budget allocated per vessel/per year for AIS subscribed services: $3-6k. Table 1 below provides details of the relevant ranges.
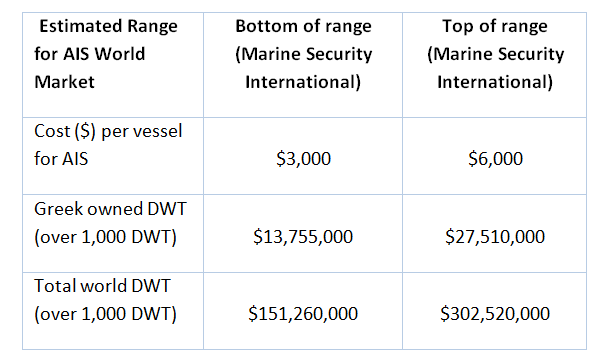
Table 1: Estimated AIS World Market
According to a Markets and Markets report (2014) North America had the largest AIS market share 30.2%, followed by Europe 27.6% and Asia-Pacific 11.7%. India is the fastest-growing country, driven by investments in Maritime Surveillance. This highlights the global AIS market is dominated by vessel-based platforms, including commercial and passenger vessels, small recreational boats, crafts, and yachts.
AIS packages include terrestrial and satellite coverage, provided by companies including: Marine Traffic, FleetMon Clearwater, Lloyd’s List Intelligence, and Netpas. However, having AIS and not using it is an issue. A representative from FleetMon stated: “SE Asian boats are usually without AIS or if in the act of illegal fishing will turn off AIS”. This led the Indonesian government to insist all vessels have at least GPS fitted, a low cost way of tracking vessels; however, if a captain wants to disable this, he is generally able to do so and will only be caught if a Coastguard vessel comes across him on the water.
AIS Exposed Vulnerabilities and Attacks
Since 2002 AIS was introduced to supplement existing safety systems, required on any international ship with gross tonnage of 300+, and all passenger ships regardless of size with future installations expected to rise to over a million units.
However, AIS can be exploited by various subversive players, as the earlier AIS protocols were designed with almost no obvious security considerations. Consequently it is possible to exploit vulnerabilities in the AIS internet provider systems, so-called implementation [Software–specific SW ‘messing with the data’] threats, attacking online provider collection and visualisation of vessel information. This is relevant today as data is routinely collected via mobile apps, software, and even formatted emails.
There is also potential to attack the system through flaws in the AIS protocol itself, as Protocol-specific [RF ‘messing with the in-built commands’] transponders use instructions, through VHF gateways.
Ship Spoofing [SW/RF] threats include spoofing online providers to ships or Aids to Navigation (AtoN). False routes can be programmed to force ships to follow paths using Google Earth information, deceiving victims up to 20km away.
AIS Hijack [SW/RF] A route gateway can be hijacked, researchers Balduzzi and Wilhoit moved the Eleanor Gordon in 2013 [MMSI 367532850] from the Mississippi River in Southern Missouri, causing it to pop up in a lake in Dallas- a real digital Philadelphia Project! Not all spoofing is deliberate. MMSI numbers can simply be entered incorrectly, and algorithms can separate vessels broadcasting with the same identity. Hijackers can also hack cargo, speed, and location data etc.
RF VHF threats to AIS Communications exist wirelessly, as protocols designed in a hardware epoch before Software Defined Radio (SDR) entered the commercial scene, when hacking was difficult and expensive when neither authentication nor integrity checks were required. SDR today operates in many device applications, such as Radio/ or TV receivers, and is accessible to radio amateurs or pirates. SDR transmitters are now available relatively cheaply.
Besides RF spoofing there is ‘man in the water spoofing’ [AIS-SART RF] generating a fake man in the water distress beacon, exploiting laid down Protocols which trigger SART SOS alerts up to 60km range. These can lure victim vessels into navigating hostile or pirate-controlled seas, a serious problem as SART alerting is mandated by law.
Frequency hopping [RF]- is one example of Availability Disruption threats, including Slot starvation and Timing attacks. Frequency hopping disables AIS transponders by switching them to non-default frequencies, and can target a desired region geographically, e.g. pirates could render ships invisible upon entering Somalia territory.
Closest Point of Approach (CPA) [RF] Fake alerts can trigger a collision warning alert, or trigger an alarm estimate until time to collision, even acoustically (siren) or visually (Captain’s display console).
Then there is attacking the application layer [SW]. AIVDM (AIS) transmit messages are exchanged via wireless [RF], and processed at the application layer with back-end software. Consider booking a flight on an ‘open’ website, and entering your data in the front-end. Once input data it goes to the database (on the data server) and as you don’t see the backend, hackers can swap pieces of real or fake data in and out, changing information such as the number of passengers, crew etc. without you knowing.
Malicious software payloads [SW], e.g. Heartbleed attack, can cause buffer overflow if data input isn’t checked properly, as data may exceed the array size (too much data). SQLi is a code injection technique attacking data-driven applications (security vulnerability), where attackers spoof identity, tampering with data or destroying it etc. averaging some 4 web application attacks per month, whilst “ghost” attack generates incorrect calculations due to missing factors because an input data array is too small.
In August 2009 US Justice Dept. charged Albert Gonzalez and 2 unnamed Russians with theft of 130 million credit card numbers using SQL injection attack; such attacks on AIS system data are equally attractive options. And if all this fails it is still possible to flood devices with noise on their AIS or GPS channels, rendering them useless.
Proposed digital electronic countermeasures
Authentication must ensure transmitters are genuine, add time checks to avoid ‘replay’ data attacks, and introduce integrity tampering monitoring checks for hijack of AIS messages. Valid data content checking is needed, e.g. is the geographical information likely to be correct? AIS is a widely used-mandatory technology in marine safety, but as shown may be broken at both the implementation and protocol level as shown by Trend Micro.
As the protocol is unencrypted vessel position data can be tampered with. Shipping container lines such as Maersk are particularly vulnerable to ransom attacks (Ransomware) which cost hundreds of millions of dollars per year. AIS data can be encrypted (Warships can do this) but if nearby vessels are unable to decrypt data, the AIS safety benefits are lost, creating problems with non-encrypted, but otherwise operationally compliant, systems.
Owing to the lack of encryption and message validation it is possible to spoof AIS over RF or data server side. Very little equipment is required as transmissions are over VHF. Transmit antennae are under a metre tall and c. 20 Watts is required for short range transmission. It is easy to overpower legitimate AIS signals locally, whilst other AIS message types interfere with safe shipping. Data fields can be modified to indicate high waves, drifting mines, vessel listing, capsize, or modifying weather (meteorological and hydrological data, besides warning reports.
Software security company CyberKeel recently evaluated the top 50 container carriers’ and found 37 out of these 50 appeared open to simple attack over back-end systems, with 6 allowing harvesting of usernames, with 8 carriers controlling 38% of global trade, actually allowing “password” to access sensitive eCommerce applications! Almost 70% of malware is shared inadvertently through social media, with c. 99% of cyber-security breaches with known vulnerabilities listed in accessible national vulnerability databases (perfect information for hackers). About 90% of such breaches, however, have software patch updates containing the required security fixes available.
We can be sure that the threats to our modern digital maritime navigation-related systems are not going to disappear as the commercial value and sensitivity of data is going to increase. It is incumbent upon all service providers and users to work together to improve security of our electronic aids against deliberate attack. The sheer size of geospatial vectors in raster and point cloud data make them perfect targets for computer-based learning algorithms. We should all be concerned at the thought of ‘bad actors’ -rogue individuals and organisations, and enemy states that can generate ‘fake geography’, or imaginary platforms. Secure location data, and technology that can accurately provide it are fundamental to our daily lives and activities. Without these validated services, we could easily fall prey to digital pirates at considerable financial cost, or even risk life itself.
*Christopher Lavers is a Lecturer in Marine Engineering, and has taught Maritime and Remote Sensing topics at the University of Plymouth at Britannia Royal Naval College since 1993. He has published 200 articles on technical subjects and a dozen science-art exhibitions since 1988, as well as two books, with others forthcoming. He is a member of the Institute of Physics Environmental Physics Committee, and Convenor of the Special Interest Group in Conservation and Indigenous Communities of the Remote Sensing and Photogrammetry Society. He is Subject Matter Expert (Radar and Telecommunications) at Britannia Royal Naval College.
He has spoken on Radio 4’s Material World programme, Radio Devon and Plymouth Sound radio several times. He is husband to Anne, a father to five, and a grandfather to boot.
Writes: Reeds Professional Books, Reeds Marine Engineering & Technology Series
Author of : Reeds Vol 6: Basic Electrotechnology for Marine Engineers, Reeds Introductions: Principles of Earth Observation for Marine Engineering Applications, Reeds Introductions: Essential Sensing and Telecommunications for Marine Engineering Applications, Reeds Introductions: Physics Wave Concepts for Marine Engineering Applications, Reeds Vol 7: Advanced Electrotechnology for Marine Engineers, Reeds Vol 14: Stealth Warship Technology